Whether in the private sector, in public authorities or in huge companies - digitalization does not work without networks. These ensure secure and efficient data exchange and communication across different ranges.
However, this requires a well thought-out infrastructure that works flawlessly at all points. How this can be set up depending on the specific area of application is defined in network technology. We have summarized the basics of this for you here.
A network is a connection between at least two IT devices. This connection can have different structures (e.g. wired or wireless) and cover different ranges.
The aim is to enable data exchange, communication and shared use of, for example, storage space, programs or data.
You can only read this blog post, edit a document with colleagues or connect your smartphone to Bluetooth applications with the help of a network. There is therefore a network behind every digital interaction.
Network technology deals with precisely this question. After all, a functioning network must be well planned and regularly maintained. It is not for nothing that we speak of an infrastructure. If just one adjusting screw in the supply is not working properly, this can have an impact on the entire data transmission.
A network connects computers so that they can share resources such as computing power and memory. An operating system provides these functions. However, a network must not only function well, but also guarantee security. How exactly it should be set up is therefore extremely dependent on the location and the planned size.
You should therefore consider this before you delve deeper into network technology:
A connection in a private two-person household is completely different from a network that connects thousands of employees of a company across countries. Some network technologies are limited and particularly restrict the range and geographical extent of the network. For this reason, a distinction is made between different network types as the basis of network technology:
Local area networks:
More extensive mergers:
Networks such as LAN and WAN are often connected and there are technologies and protocols that are used in both networks. A clear separation is therefore not always possible. You can find more detailed information on this topic in our blog post Network types: Overview of types and areas of application.
A virtual private network (VPN) also hides both the IP address and the location. It can be assigned to one of the network types mentioned and can therefore be seen as a type of add-on.
Another important foundation of network technology is the choice of the right concept. This is primarily about the role that the devices involved in the network take on:
Another central part of creating a network is the type of connection. There are many different ways to connect the various components with each other. They differ in their advantages and disadvantages.
We would like to present some of them to you here as examples. Please note, however, that there are others.
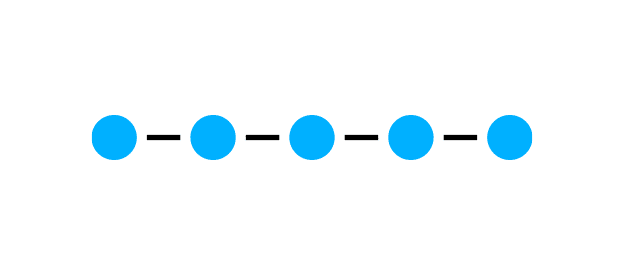
The linear structure can be compared to the way a string of lights works. The individual IT devices are connected in series. If one component fails, there is a breakdown and data cannot be forwarded.
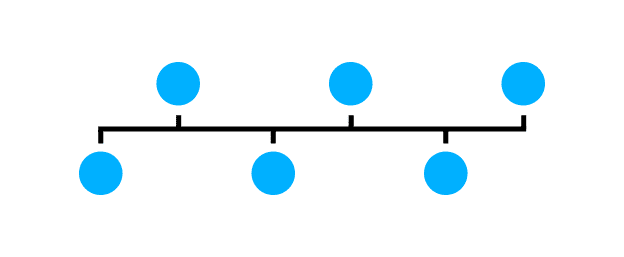
With the bus topology, all hosts are connected to a common line. If one computer fails, all others are still connected via the main line.
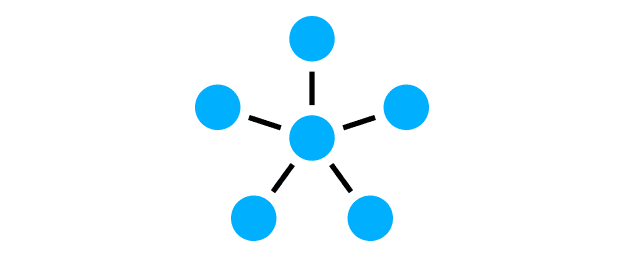
The star topology describes the networking of several devices that are all connected to a central system (usually a network server). The structure of the server in the middle and the computers arranged around it resembles a star.
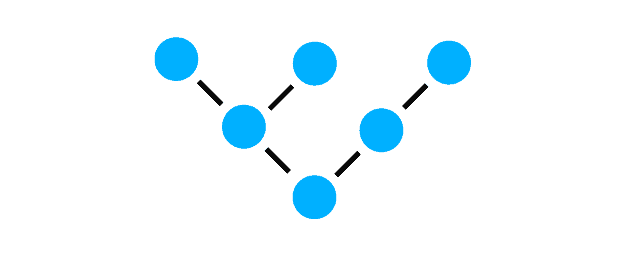
The tree topology combines properties of star and bus networking. Basically, several star topologies are connected hierarchically via a main line.
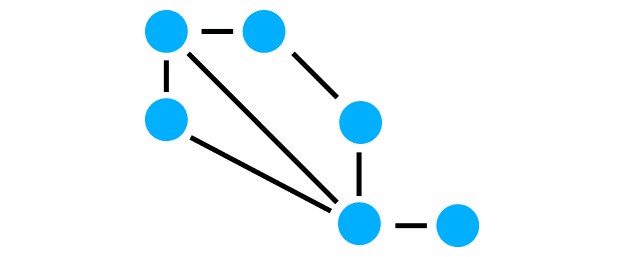
Meshed networks are closely interwoven and each network node is connected to one or more others.
To create a network, at least two computers or other IT end devices must be connected to each other. Data can be transmitted via copper or fiber optic cable, WLAN or WiFi or a combination of these.
In order to be able to establish such a connection at all, appropriate hardware is required in addition to the end devices:
A hub, for example, brings devices together in a LAN network. However, it does not differentiate between the individual participants. A data packet is therefore always sent to all users and not just to the desired recipient.
Switches close this security gap (and the resulting high level of data exchange). They work like hubs, but identify all network participants individually based on their assigned MAC address (more on this in the section on network addresses). This means that only those users receive data packets that are intended for them.
Would you like to know the exact difference between a switch, a hub and a router? Then read our blog post “Switch vs. hub vs. router: key differences”.
In order to create networks beyond LANs, network technology uses devices that can read IP addresses. This is the only way to enable communication outside a local network and use of the Internet.
Routers are usually used for this purpose. In contrast to hubs and switches, these can read and assign IP addresses. In this way, data can be forwarded either internally or externally to the addressed location.
Layer 3 switches are somewhat newer and therefore less frequently used. These are a combination of router and switch. Their use is particularly useful in large networks, as these switches sometimes have a higher speed than pure routers.
Switches and routers can also be expanded with modules and transceivers that act as both transmitters and receivers.
This high-performance hardware makes data available to authorized network participants locally and globally, permanently and centrally. It thus forms the center of a client-server network and ensures fail-safe and fast communication - even in huge connections.
Depending on the specific device, network servers meet distribution requirements from home networks to huge corporate structures. In addition to efficient data transmission, they ensure that the network functions more securely.
You can read more about this in our blog post: "Network servers: the heart of a functioning infrastructure".
Different network addresses are used when setting up a network. Depending on the purpose and data transmission layer of the standardized OSI layer model (see OSI model), these take on different tasks. Basically, however, the main function is to be able to communicate in a targeted manner - i.e. to mediate between sender and receiver as required.
Two of the network addresses that are fundamental to network technology are briefly introduced here:
The MAC address (Media Access Control address) is used by switches, for example. It identifies different network locations and can transmit data and messages in a targeted manner. Each host in the network is given an individual 48-bit MAC address. This allows a data packet to be transmitted from a specific recipient within the local connection - and only to that recipient.
The purpose of an IP address (Internet Protocol address) is to be able to track and uniquely identify a network-compatible device across different networks. It therefore forms the basis for using the Internet and can address servers or IT devices all over the world beyond local connections.
A further distinction is made here between IPv4 and IPv6 addresses. The former are currently more common, but are limited to 4.3 billion combinations. As a result, internet users are constantly assigned a new IP address and it is only possible to track an activity together with a time stamp.
The IPv6 address is intended to counteract this address shortage. Internet providers have been gradually converting their connections for several years now. The expansion is made more difficult by the fact that many customers still only have IPv4-capable end devices.
The many components and networking types show: Building a network is complex and requires a precise plan. A lot has to be taken into account, especially for extensive connections. The OSI layer model therefore exists to simplify the path to functioning communication protocols and computer networks. Networks use special addresses to identify senders and receivers of data packets. These addresses vary depending on the function, application and protocol layer, so that each OSI layer uses its own addresses, e.g: Application layer: e-mail addresses, URL or domain.
The manufacturer-independent reference model is considered the standard in network technology and assigns tasks to seven layers. This is particularly advantageous if an error occurs, as in this case you can quickly find out where it can be rectified.
In short, it looks like this:
| Layer | Designation | Function |
|---|---|---|
| 7 | Application Layer | User interface of network applications, communication between application processes of the end devices |
| 6 | Presentation Layer | Conversion of data formats into network formats |
| 5 | Session Layer | Connections between instances of communicating devices, reporting of errors |
| 4 | Transport Layer | End-to-end encryption, secure data transmission |
| 3 | Network Layer | Data exchange beyond local networks, defining the IP address |
| 2 | Data Link Layer | Identification and addressability through MAC addresses, securing data transmission through protocols |
| 1 | Physical Layer | Physical conditions (e.g. definition of cable properties, connection components ...) |
Network security is an important and crucial aspect of protecting data from threats. Firewalls play a key role in this by monitoring network traffic and blocking unwanted access. Access points secure wireless connections with strong security protocols such as WPA3. You can find more information on network security in our specialist knowledge "IT Security in Companies: Importance and Solutions".
Encryption protects data by converting it into an unreadable format that can only be decrypted with a special key. Authorization ensures that only authorized users have access to sensitive information, often through methods such as passwords and two-factor authentication. You can find more information on password security in our blog post "Secure password practice: tips for creating and managing robust passwords".
Despite these protective measures, the risk of hacker attacks and threats remains. Therefore, regular updates, strong passwords and security awareness are important to keep networks secure.
The information in this article is a good basis, but only scratches the surface of network technology. Nevertheless, it forms a solid foundation for setting up your own network. Network technology encompasses numerous exciting topics, which we cover in detail in our blog. So take a look at our individual blog posts for more in-depth information.
This is where we come in: at IT-Planet, you can get exactly the components you need for networks of various sizes, from switches and routers to network servers. You have the choice between brand new and top refurbished hardware from well-known brands such as APC, Cisco, HPE Aruba, SonicWall or Teltonika.
Do you have any questions? We will be happy to advise you in detail. Just get in touch using our contact form.


There are various ways to protect your network. You should take this into account when planning your IT infrastructure. Protection is a multi-layered process that involves a combination of hardware and software.
How broadly you position yourself in terms of cyber security depends on the type and size of your network and the sensitivity of your data: The security aspects of a company that works with customer data spread across several locations are usually different to those of a private individual.
Here, requirements quickly become necessary that go beyond the use of strong passwords and anti-virus software.
In this blog post, we have shown what this can look like, for example: IT security in companies: Importance and solutions
There is hardly any data that is not exchanged via a network or at least stored on a device that is part of such a network. Contact details, medical information, credit information - all of this can be fatal for those affected in the wrong hands.
However, the destruction of hardware and the information it contains (e.g. due to a burst pipe) also poses a significant risk.
Companies in particular should therefore be prepared for malware, ransomware, phishing and external influences.
The hardware you need to set up a network depends on the type and size of the network. In home networks, a computer with a network card and a router are often sufficient to establish a connection to the Internet. A slightly faster connection can be achieved using network cables.
In very large networks in a company or spread across different locations, several servers, switches, routers and end devices are often required.
Networks are indispensable both in everyday life and in the corporate context. They connect several devices with each other and thus enable the exchange of data and the sharing of resources between them. Without this technology, you would not be able to access the Internet, send emails or communicate with your printer… You would only be able to use local services and programs.
Network technology is concerned with setting up, securing and maintaining networks. Experts in this profession plan and test all hardware and software components that enable secure communication between different devices.