IT security for companies is an important part of any corporate strategy. In view of the increasing threats posed by cyber attacks, companies must integrate modern IT security solutions into their IT infrastructure. This includes protective measures against data loss, phishing attacks and ransomware. For attackers aiming to blackmail, financially enrich themselves or damage their reputation, companies are a far more worthwhile target than private individuals. This makes IT security (also known as cybersecurity) in companies an area that should not be neglected under any circumstances.
But attackers are becoming more and more insidious and the threat has been increasing for several years - so where do you start with security precautions? We provide you with an overview of this extensive topic, which can serve as an initial orientation.
IT security refers to a holistic approach to protecting computer systems, networks and data from a variety of threats arising from the digital environment. This includes protection against unauthorized access, manipulation or theft of sensitive information as well as against damage that can be caused by cyber attacks.
IT security measures aim to ensure the confidentiality, integrity and availability of data and systems. This includes the implementation of firewalls, antivirus software, encryption technologies, access controls, security policies and employee training programs.
As the threat landscape is constantly changing, IT security requires continuous monitoring, adaptation and updating to keep pace with the latest threats and maintain an appropriate level of protection.
In an IT security concept, there are various protection goals that can be weighted differently depending on the industry and infrastructure. However, the three cornerstones of information security always remain relevant everywhere.
The three primary objectives (also known as the CIA triad) are defined by the BSI (German Federal Office for Information Security):

Hackers, phishing emails and other online dangers are not the only threats. Physical risks such as force majeure - for example lightning, fire or flooding - must also be taken into account in your security concept. It also includes protective measures against identity theft, keyloggers or spyware that can spy on sensitive data.
IT security includes all measures to protect hardware and software systems and the files and information stored on them. This includes technical solutions such as spam filters, a reliable network firewall or an intrusion detection system to detect suspicious activities at an early stage. The use of VPNs also ensures secure access to your systems, especially for mobile workstations. Regular security audits help to identify vulnerabilities in the IT infrastructure early and address them effectively. Additionally, a clear emergency strategy, including a communication plan, ensures swift action in the event of a cyberattack or system failure.
The concept of zero-trust architecture also plays a central role in comprehensive security. This is based on the principle of least privilege, whereby each user can only access the systems and information they need for their work. In addition, measures such as whitelisting and blacklisting prevent unwanted programs or users from gaining access.
Important: IT security is the responsibility of the management. It must ensure that sufficient resources and specialist staff are available to implement security measures such as cryptography, HTTPS or the use of security tokens on a permanent basis.
Malware is an artificial word for "malicious software", i.e. malicious software that is smuggled into your network. This can infect your infrastructure in the form of viruses, Trojans or computer worms for example. In the corporate context, however, ransomware plays a particularly important role.
A threat to websites and thus blocked traffic can be caused by DDoS attacks (Distributed Denial of Service). These attacks use distributed networks and botnets in an attempt to cause damage to the company. Botnets can be used not only for negative but also for positive purposes.
According to the BSI, ransomware is the biggest and most common threat to IT security in companies. The infiltrated malware ensures that devices, servers or parts of them are blocked for you and all other users. With access to your own data behind them, the attackers make demands - usually in the form of a ransom demand.
Access to devices, servers or parts of the hardware is blocked by the infiltrated malicious software. This step is followed by demands, usually in the form of a ransom. During this period, you have no access to your own data, which can have devastating consequences. However, it is not advisable to pay these demands. For the hackers, only one thing is important: to remain anonymous and unrecognized.
Phishing is an attempt by criminals to obtain confidential data (e.g. access or bank details) using fake emails (or other messages such as text messages). The BSI (German Federal Office for Information Security) provides a checklist (only in german) for phishing attacks. While the mass emails here are rather impersonal, spear phishing attacks are targeted at employees of specific companies or industries. They are researched in detail and can look like internal company emails. Whaling goes one step further - the fake emails are aimed at managers and other high-ranking people in the company.
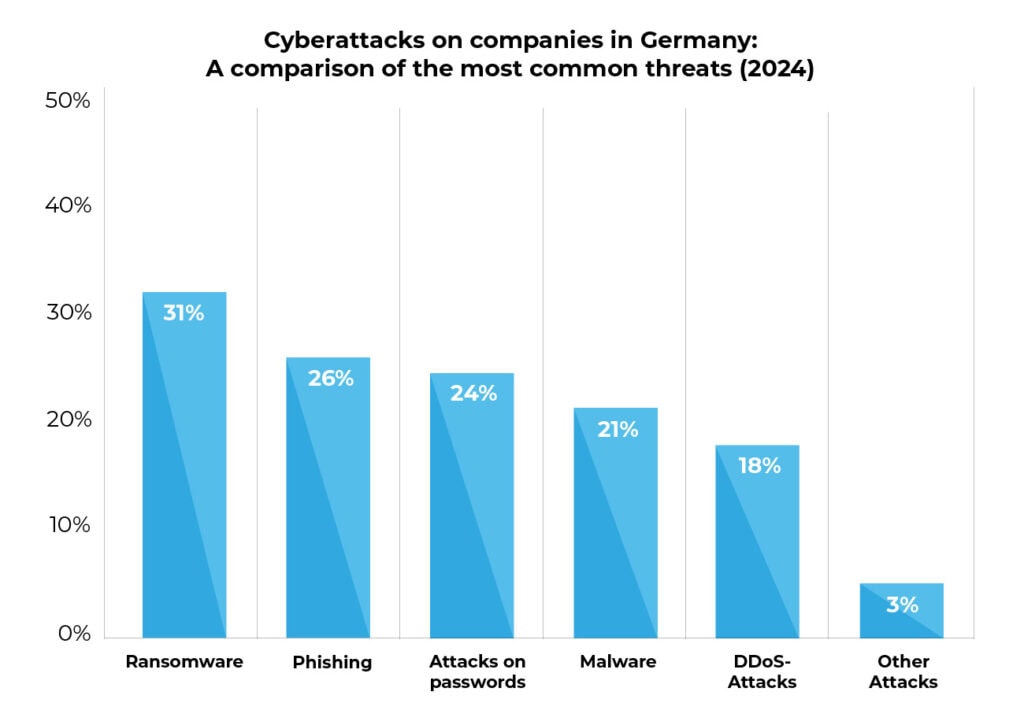
Proportion of companies affected by type of cyberattack. The data is based on the Bitkom study ‘Wirtschaftsschutz 2024’ in cooperation with the Federal Office for the Protection of the Constitution (BfV). Source: bitkom.org, as of August 2024.
When data is deliberately or unintentionally altered, for example by manipulating files or information, this is known as data manipulation. This is often used to create a false image or to adapt data for specific purposes. Thanks to the use of artificial intelligence, social engineering attacks can now look so deceptively real that it is becoming increasingly difficult to distinguish between real and fake messages.
This form of manipulation falls under the term “social engineering”, which in the field of IT security refers to attacks in which people are tricked into disclosing confidential information. Human weaknesses are specifically exploited in order to carry out espionage or sabotage.
How can you protect yourself from social engineering?
Why human behavior is in focus:
Social engineering shows that security depends not only on technology, but also on the people who use it. Training on data protection, secure passwords and the detection of phishing attempts is crucial to minimize the human vulnerability.
The Federal Office for Information Security has published a report on IT security in Germany in 2022. This makes it clear how much and in what way the threat has increased in recent years.
The most common security risks for companies were identified:
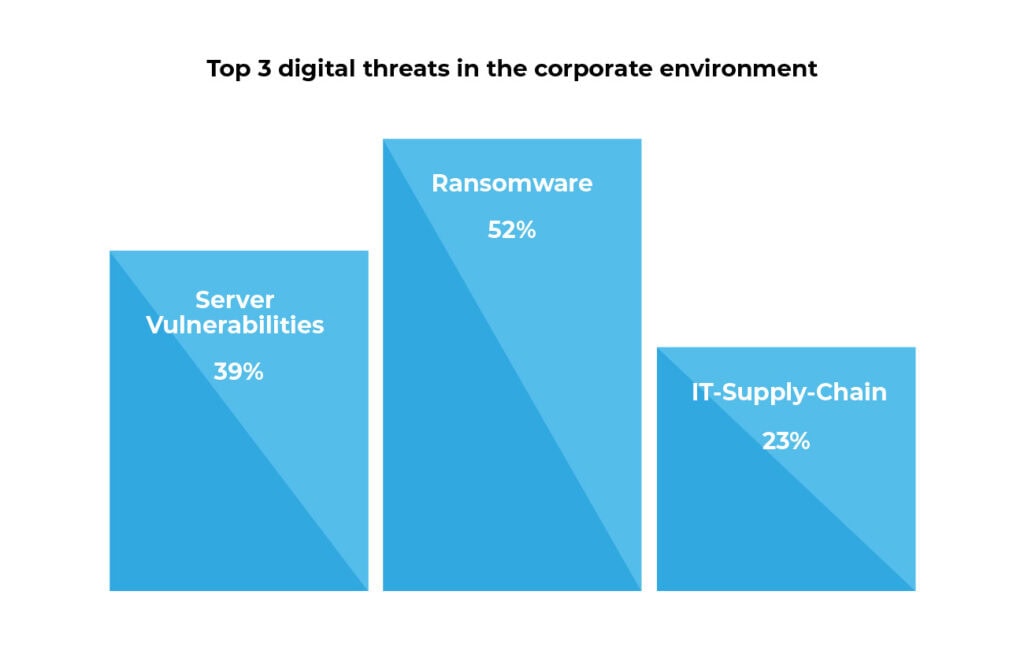
However, this does not mean that the other risks mentioned in this article should be neglected. IT security should always be reliable and as broad-based as possible.
In addition, measures such as forensic IT analysis are essential in the event of security incidents in order to uncover vulnerabilities and trace attack paths. Even supposedly minor vulnerabilities, such as program errors, should be taken seriously and rectified quickly, as they can trigger potentially serious security problems.
In the event of a cyberattack, not only internal company data but also customer data is affected. Therefore, companies are obliged to implement appropriate technical and organisational measures to effectively protect personal data and trade secrets. IT security in companies is therefore not mandatory, but sometimes follows industry-specific legal regulations.
These are stipulated, for example, by the EU General Data Protection Regulation and the IT Security Acts 1.0 and 2.0 (as of June 2024). Critical infrastructure companies must comply with particularly strict IT security requirements. These include nuclear power plants, hospitals and telecommunications companies. They even have to report possible attacks to an official body, namely the Federal Office for Information Security (BSI).
However, the fact that there is a separate federal office for this topic shows that a lack of IT security is no joke, even in a free market economy. Cybercrime ultimately affects everyone - from small and medium-sized enterprises (SMEs) to large corporations. Violations of IT security regulations can result not only in fines but also in significant reputational damage, making proactive security management essential. Regular training and employee awareness programmes can help minimise human error as a security risk and ensure compliance with legal requirements.
Every company should set up a risk management system in order to be prepared for cyber threats. This management includes the systematic identification, assessment and control of risks.
The following steps:
An IT security audit in the form of a checklist can also help to review the company's security situation in the event of a cyberattack or similar threat. It shows numerous steps to improve security precautions and document the current status. This way, you are securely positioned once the measures have been completed. You can download the checklist here:
A word at this point: This article is intended to help you understand the importance and scope of the topic and does not constitute legal advice. If you have any questions, we recommend that you contact an IT security manager or consult the official website of the BSI.
As the digital transformation progresses, so too do potential points of risk that you need to consider in your IT security strategy. Changes in working behavior, which have developed particularly since the coronavirus pandemic, also play a role here.
More and more people are working remotely. Whether working from home or on the move from a café - security measures need to be just as effective here as they are on-site at your company. However, this is often not the case. Dialing into public, sometimes unsecured networks is a major problem here.
As a result, the blurred boundaries between private and business use of devices are a problem for IT security in companies. Installing internal company messengers on a private smartphone, for example, is already a violation of the GDPR according to the current legal situation. The reason for this is the data that may not be stored outside company-internal devices and applications in the first place.
Another increasing risk comes from the growing Internet of Things (IoT). Smart devices of all kinds - whether smart homes or intelligent purchases in the office - increase the potential attack surface in cyberspace.
There are measures that are indispensable and can often be implemented in-house without IT specialists. They are fundamental because they form the absolute basis of IT security in companies - but also everywhere else. The implementation of these measures is also strongly recommended by the BSI:
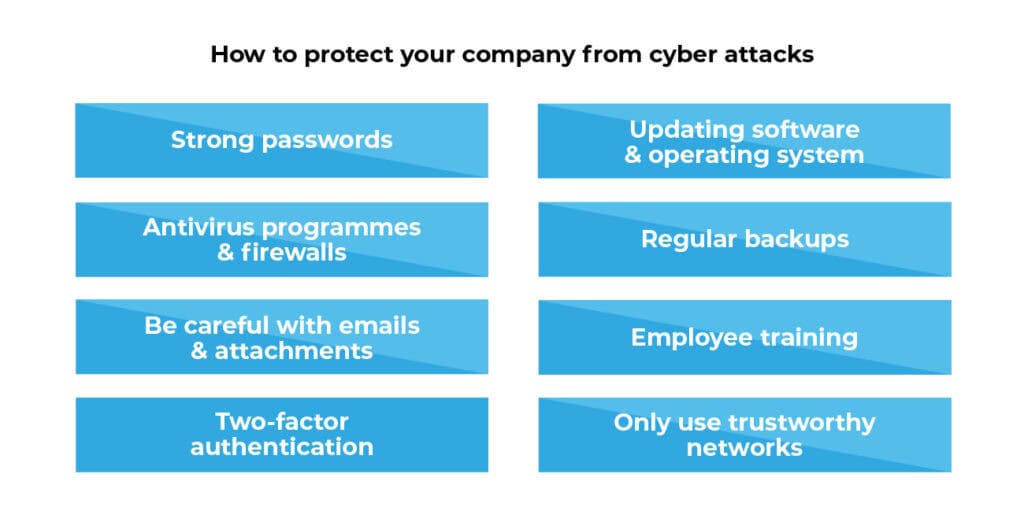
You should never rest on your laurels when it comes to good passwords and virus protection. This may be sufficient in a private environment, but your data is too important (and the guidelines are often too strict) for this to be enough.
Instead, you need a detailed security concept and IT specialists to implement it. After all, IT security is not something that is done once - it needs to be constantly adapted, because malware is also constantly evolving. In principle, your approach should always include permanent planning, implementation and monitoring.
This is facilitated by what is known as an Information Security Management System (ISMS). This defines rules and procedures to ensure IT security in companies. Large corporations in particular cannot avoid having one in order to quickly identify and rectify risks and problems. Important: Such a system is the responsibility of the management and follows a top-down approach. Decisions can therefore be made by technically competent employees (such as IT staff and GDPR officers).
The IEC standards
IEC 62443: internationally recognized standard for operators and manufacturers of industrial automation systems; protection against cyberattacks through clear rules and requirements
IEC 15408: internationally recognized standard for security assessment of IT products; security objectives through ISO/IEC 15408-1:2009 (guidelines for assessment)
When it comes to IT security in companies, it is important that all employees are trained. IT specialists and management cannot implement this alone. All people with access to company data must follow certain rules to ensure that the security concept works.
This includes, for example, the careful use of passwords, downloading updates and avoiding public Wi-Fi spots. But it is also important that your employees are able to recognize, avoid and report security risks at an early stage.
Don't forget to prevent risks that directly affect your hardware. Whether by malicious intent from outside or by accident - computers, servers and hard disks in the physical sense can also become a target. Take this fact into account in your IT security concept.
Locking your servers, data center and laptops after use can be a possible measure. To prevent data loss, backups should always be created and stored on external hard disks or in RAID systems (Redundant Array of Independent Discs).
You should also pay close attention to the specified security factors when choosing your hardware. For example, server racks are available with a fireproof design. However, it is generally worthwhile choosing high-quality components such as switches, transceivers or network servers. If you are interested in sustainable, used products, do not buy them privately, but from a reputable source.
In principle, all devices in your company should be protected against malware and viruses by virus protection programs and firewalls. We offer a wide range of excellent firewalls from well-known brands such as SonicWall and Juniper.










There is no standardized method for measuring the security level of your IT concept. Instead, you have the option of choosing the best approach for you. These are possible, for example:
White hat hackers, ethical hackers or penetration testers (pen testers) have set themselves the task of finding vulnerabilities. To do this, they put themselves in the shoes of their criminal colleagues and simulate an attack on your IT infrastructure. In the event of a gap, this can be closed at an early stage.
It is also helpful to measure the speed and ability with which your company reacts to attacks. Estimating response times and the time it takes to restore data helps to assess the security situation.
You can use security audits to regularly review your IT security measures and assess potential vulnerabilities.
Defined security metrics help with a targeted assessment. For example, you can record the number of incidents, the average remediation time or the success rate of security audits.
The BSI also offers a checklist for emergencies (only in german) if you fall victim to a cyberattack.
Cyber security starts with a well-planned and reliable IT infrastructure. It helps to create a dense architecture for the flow of information, but also to quickly isolate problems.
However, IT security in companies means more than that. Under no circumstances should you cut corners when setting up an appropriate concept, software and hardware or the personnel costs for IT staff. Everything ensures that personal data relating to your projects, employees and customers is protected against attacks.
By complying with the BSI standards, including BSI Standard 200-1, 200-2, 200-3, 200-4 and 100-4, for IT security, you also have the opportunity to obtain ISO 27001 certification. This is awarded exclusively by auditors certified by the German Federal Office for Information Security and is recognized worldwide. Proof of compliance with the standards not only gives you security, but also potential customers.
We offer secure firewalls, servers, switches and transceivers for your company to ensure comprehensive protection in the IT sector. Our well-known brands include SonicWall for firewalls, Cisco and Juniper for switches and HPE Aruba for servers. Would you like to inquire about a project with us? Please use our inquiry form!



A firewall is not the same as virus protection; they are two different security technologies with their own specific tasks. While a firewall monitors the network and blocks unwanted access, virus protection software detects and removes malicious software. The firewall acts as a barrier between the internal network and the outside world (the Internet). It protects against unauthorised network access such as hackers or viruses. Antivirus software, on the other hand, is software that scans files, programmes and visited websites for signs of threats, blocks them and, if necessary, removes them (if a threat is detected). This protects against malware, viruses, worms, Trojans and ransomware. A combination of a firewall and antivirus software is ideal for ensuring a comprehensive level of security.
Zero trust refers to a security concept in which neither internal nor external network access is automatically trusted. Instead, every access is first classified as potentially dangerous and then checked and verified. The aim is to continuously improve a company's security. Each user or device is only granted the rights necessary for the task at hand. Zero Trust Security thus combines identity and access management, network segmentation, continuous monitoring and various security solutions:
In addition, technologies such as Zero Trust Network Access (location-independent, secure access to resources), Software Defined Perimeter (dynamic firewall for access to resources) and Next-Generation Firewalls (advanced security features) should be used.
The BSI (Federal Office for Information Security) offers recommendations, guidelines, certifications and support for improving IT security. It is the central German cyber security authority and certification body for IT products and services. In addition, the BSI provides practical minimum standards (e.g. BSI Standard IT Baseline Protection). It also offers recommendations for information security management (ISMS). These include employee training in security awareness, secure password use, regular updates of software and operating systems, and backups of important data.
ISMS (Information Security Management System) refers to a systematic approach to protecting sensitive data and information from cyber risks. This improves the structure of a company's security. Vulnerabilities can be identified, remedied and permanently reduced through appropriate measures. In addition, an ISMS supports compliance with data protection regulations such as the GDPR or other regulatory requirements. An ISMS is verified by ISO 27001 certification. An ISMS encompasses IT, organisation, personnel and physical security in the form of guidelines, procedures and technologies. The aim is to ensure the confidentiality, integrity and availability of data.
A penetration test is a simulated cyber attack on your own system, network or application in order to identify and remedy vulnerabilities or security gaps. This tests whether the system is adequately protected against a real attacker or hacker. Various techniques and methods are used (similar to a real hacker attack) to test security at different levels. A test shows how the system or application responds to attacks and reveals hidden security gaps that can then be remedied.
Companies can measure and evaluate their IT security by carrying out the following steps:
In order to obtain ISO 27001 certification, companies must set up an information security management system (ISMS) in accordance with the requirements of ISO 27001 and implement this within the company. In addition, internal audits must be carried out, followed by a certification audit of the company by an accredited body.
Companies must comply with various legal regulations relating to IT security, including:
The most common security risks for companies are malware, phishing attacks, software vulnerabilities, human error and insecure system configurations.
The most important steps for implementing an IT security concept in a company are: